For some reason it triggered (even without --bug-oracle) for the following contract:
/ityfuzz/cli/target/release/cli -c ETH --onchain --onchain-block-number 17521638 -f --target 0xa5564a2d1190a141cac438c9fde686ac48a18a79
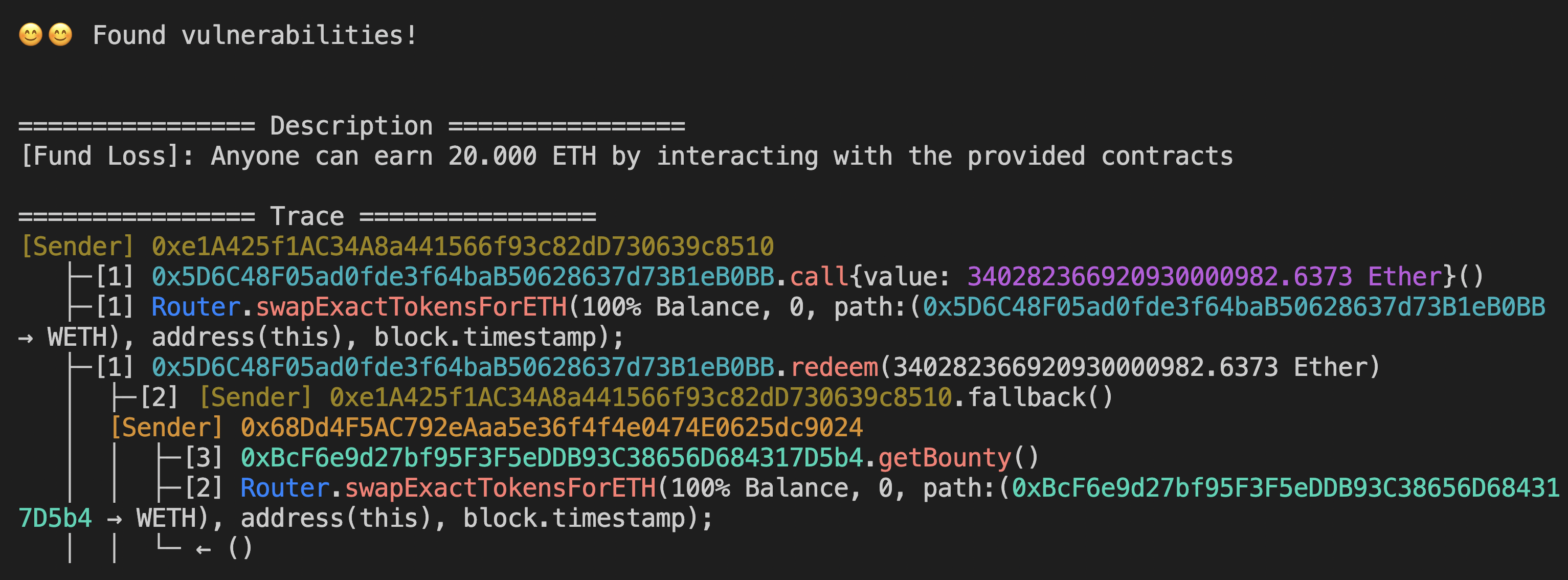
😊😊 Found violations!
================ Oracle ================
[bug] bug() hit at contract 0x5b19bd330a84c049b62d5b0fc2ba120217a18c1c
================ Trace ================
Begin
{"caller":"0x68dd4f5ac792eaaa5e36f4f4e0474e0625dc9024","contract":"0xd96f48665a1410c0cd669a88898eca36b9fc2cce","data":"harvest(0x38ea452219524bb87e18de1c24d3bb59510bd783,0x00,0x000000001a000000000000000000000000000000000000000000000000004d4d) with None ETH (66c6bb0b00000000000000000000000038ea452219524bb87e18de1c24d3bb59510bd7830000000000000000000000000000000000000000000000000000000000000000000000001a000000000000000000000000000000000000000000000000004d4d)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":0,"additional_info":[1]}
== {"caller":"0x8ef508aca04b32ff3ba5003177cb18bfa6cd79dd","contract":"0xaf5191b0de278c7286d6c7cc6ab6bb8a73ba2cd6","data":"transfer(0x8439ac976ac597c71c0512d8a53697a39e8f9773,0x0000000000000000000000000000000000000000000000000000000000000000) with None ETH (a9059cbb0000000000000000000000008439ac976ac597c71c0512d8a53697a39e8f97730000000000000000000000000000000000000000000000000000000000000000)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":1,"additional_info":[255]}
== {"caller":"0x8ef508aca04b32ff3ba5003177cb18bfa6cd79dd","contract":"0x101816545f6bd2b1076434b54383a1e633390a2e","data":"Stepping with return: 307830303030303030303030303030303030303030303030303030303030303030303030303030303030303065643030303030303030303030303030303033343064 with None ETH (00000000000000000000000000000000000000000000000000ed0000000000000000340d)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":1,"additional_info":[255]}
{"caller":"0x35c9dfd76bf02107ff4f7128bd69716612d31ddb","contract":"0x4d73adb72bc3dd368966edd0f0b2148401a178e2","data":"withdrawNative(0xcc0d7af1f809dd3a589756bba36be04d19e9c6c5,0x0000000000000000000000000000000000000000000000000000000000000000) with None ETH (07b18bde000000000000000000000000cc0d7af1f809dd3a589756bba36be04d19e9c6c50000000000000000000000000000000000000000000000000000000000000000)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":0,"additional_info":[1]}
== {"caller":"0x35c9dfd76bf02107ff4f7128bd69716612d31ddb","contract":"0x4d73adb72bc3dd368966edd0f0b2148401a178e2","data":"Stepping with return: with Some(0x000000000000000000000000000000000000fb8000000000006c000000000000_U256) ETH (00000000)","value":"0x000000000000000000000000000000000000fb8000000000006c000000000000","flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":1,"additional_info":[255]}
{"caller":"0x8ef508aca04b32ff3ba5003177cb18bfa6cd79dd","contract":"0x5b19bd330a84c049b62d5b0fc2ba120217a18c1c","data":"updateHash(0x406f,0x,0x0000000001000018001ff300000000000b0b0b0b0b0b0b0b0b6f800000003055,0x) with None ETH (704316e5000000000000000000000000000000000000000000000000000000000000406f00000000000000000000000000000000000000000000000000000000000000800000000001000018001ff300000000000b0b0b0b0b0b0b0b0b6f80000000305500000000000000000000000000000000000000000000000000000000000000a000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":0,"additional_info":[255]}
{"caller":"0x8ef508aca04b32ff3ba5003177cb18bfa6cd79dd","contract":"0x5b19bd330a84c049b62d5b0fc2ba120217a18c1c","data":"updateHash(0x0000,0x,0xff00ffffffffffffffffffffffb2b2b2b2b2b2b2b2ffffff0000000000000000,0x) with None ETH (704316e500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080ff00ffffffffffffffffffffffb2b2b2b2b2b2b2b2ffffff000000000000000000000000000000000000000000000000000000000000000000000000000000a000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":0,"additional_info":[255]}
{"caller":"0xe1a425f1ac34a8a441566f93c82dd730639c8510","contract":"0x5b19bd330a84c049b62d5b0fc2ba120217a18c1c","data":"withdrawNative(0x01,0x06d538690af257da524f25d0cd52fd85b1c2173e,0xd8772edbf88bba2667ed011542343b0eddacda47,0x0000000000000000000000000000000000000000000000000000000000000000) with None ETH (22c10776000000000000000000000000000000000000000000000000000000000000000100000000000000000000000006d538690af257da524f25d0cd52fd85b1c2173e000000000000000000000000d8772edbf88bba2667ed011542343b0eddacda470000000000000000000000000000000000000000000000000000000000000000)","value":null,"flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":0,"additional_info":[1]}
== {"caller":"0xe1a425f1ac34a8a441566f93c82dd730639c8510","contract":"0x5b19bd330a84c049b62d5b0fc2ba120217a18c1c","data":"Stepping with return: with Some(0x0000000000000000000000000000000000000000000000000000000000000000_U256) ETH (00000000)","value":"0x0000000000000000000000000000000000000000000000000000000000000000","flashloan":"earned: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512, owed: 0x00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000_U512","direct_data":[],"layer":1,"additional_info":[255]}