Generate an IAM policy from AWS, Azure, or Google Cloud (GCP) calls using client-side monitoring (CSM) or embedded proxy
Important
The Azure and Google Cloud providers are in preview and may produce incorrect outputs at this time
Pre-built binaries for Windows, macOS and Linux are available for download in the project releases.
Once downloaded, place the extracted binary in your $PATH (or execute in-place). For macOS users, you may need to allow the application to run via System Preferences.
To build and install this application, clone this repository and execute the following from it's base:
go install
You must have Go 1.16 or later installed for the build to work.
You may also install this application using a Homebrew tap with the following command:
brew install iann0036/iamlive/iamlive
- Lambda Extension (AWS only)
- Docker
- GitHub Action (with Terraform)
To start the listener, simply run iamlive in a separate window to your CLI / SDK application. You can use Ctrl+C to exit when you are done.
You can optionally also include the following arguments to the iamlive command:
--provider: the cloud service provider to intercept calls for (aws,azure,gcp) (default: aws)
--set-ini: when set, the .aws/config file will be updated to use the CSM monitoring or CA bundle and removed when exiting (default: false) (AWS only)
--profile: use the specified profile when combined with --set-ini (default: default) (AWS only)
--fails-only: when set, only failed AWS calls will be added to the policy, csm mode only (default: false) (AWS only)
--output-file: specify a file that will be written to on SIGHUP or exit (default: unset)
--refresh-rate: instead of flushing to console every API call, do it this number of seconds (default: 0)
--sort-alphabetical: sort actions alphabetically (default: false for AWS, otherwise true)
--host: host to listen on for CSM (default: 127.0.0.1)
--background: when set, the process will return the current PID and run in the background without output (default: false)
--force-wildcard-resource: when set, the Resource will always be a wildcard (default: false) (AWS only)
--mode: the listening mode (csm,proxy) (default: csm for aws, otherwise proxy)
--bind-addr: the bind address for proxy mode (default: 127.0.0.1:10080)
--ca-bundle: the CA certificate bundle (PEM) to use for proxy mode (default: ~/.iamlive/ca.pem)
--ca-key: the CA certificate key to use for proxy mode (default: ~/.iamlive/ca.key)
--account-id: the AWS account ID to use in policy outputs within proxy mode (default: 123456789012 unless detected) (AWS only)
--debug: dumps associated HTTP requests when set in proxy mode (default: false)
Basic Example (CSM Mode)
iamlive --set-ini
Basic Example (Proxy Mode)
iamlive --set-ini --mode proxy
Basic Example (Azure)
iamlive --provider azure
Basic Example (Google Cloud)
iamlive --provider gcp
Comprehensive Example (CSM Mode)
iamlive --set-ini --profile myprofile --fails-only --output-file policy.json --refresh-rate 1 --sort-alphabetical --host 127.0.0.1 --background
Comprehensive Example (Proxy Mode)
iamlive --set-ini --mode proxy --profile myprofile --output-file policy.json --refresh-rate 1 --sort-alphabetical --bind-addr 127.0.0.1:10080 --ca-bundle ~/.iamlive/ca.pem --ca-key ~/.iamlive/ca.key --account-id 123456789012 --background --force-wildcard-resource
The arguments may also be specified in an INI file located at ~/.iamlive/config.
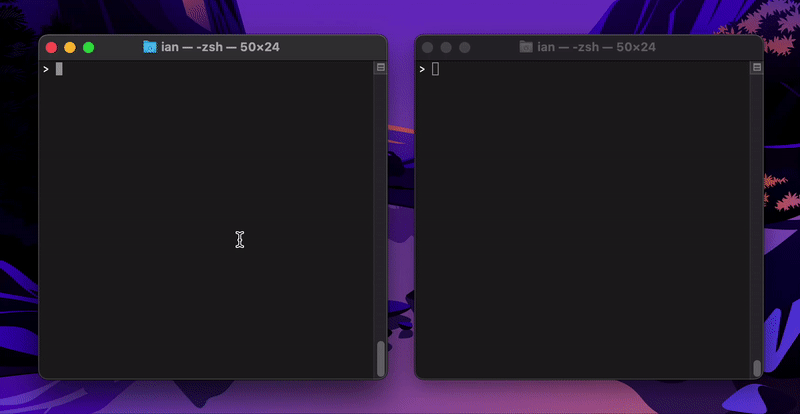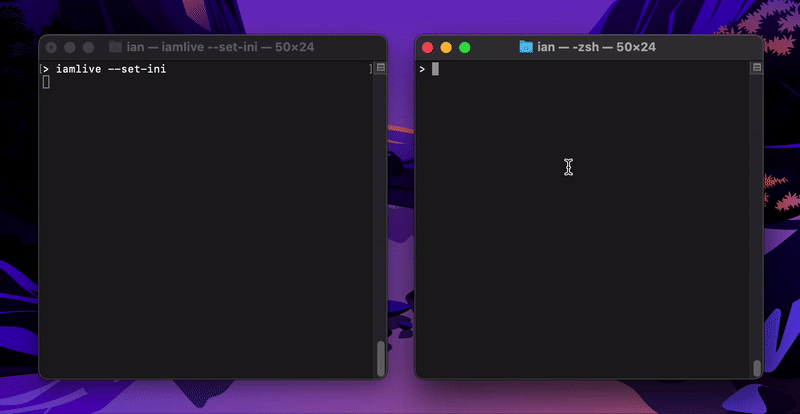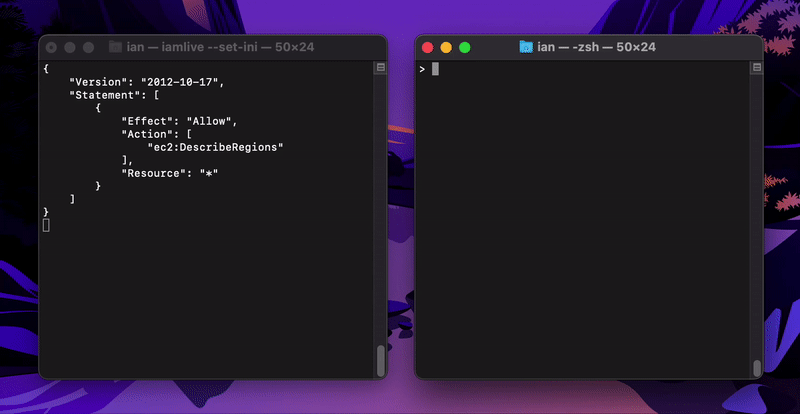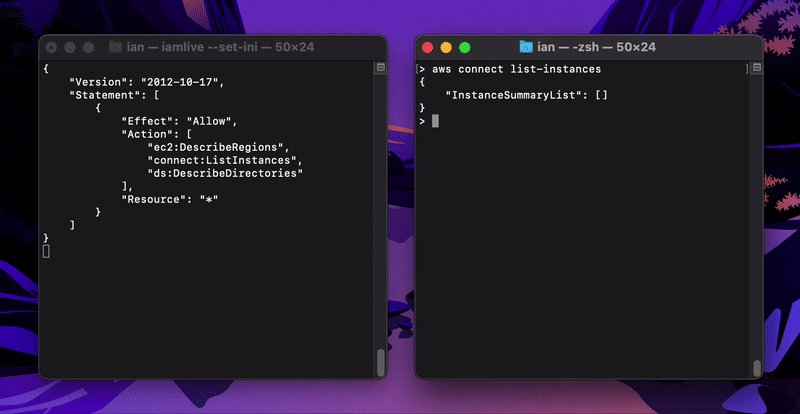
Client-side monitoring mode is the default behaviour for AWS and will use metrics delivered locally via UDP to capture policy statements with the Action key only (Resource is only available in proxy mode).
CSM mode is only available for the AWS provider.
To enable CSM in the AWS CLI, you should either use the --set-ini option or add the following to the relevant profile in .aws/config:
csm_enabled = true
Alternatively, you can run the following in the window executing your CLI commands:
export AWS_CSM_ENABLED=true
To enable CSM in the various AWS SDKs, you can run the following in the window executing your application prior to it starting:
export AWS_CSM_ENABLED=true
export AWS_CSM_PORT=31000
export AWS_CSM_HOST=127.0.0.1
Proxy mode will serve a local HTTP(S) server (by default at http://127.0.0.1:10080) that will inspect requests sent to the AWS endpoints before forwarding on to generate IAM policy statements. The CA key/certificate pair will be automatically generated and stored within ~/.iamlive/ by default.
To set the appropriate CA bundle in the AWS CLI, you should either use the --set-ini option or add the following to the relevant profile in .aws/config:
ca_bundle = ~/.iamlive/ca.pem
Alternatively, you can run the following in the window executing your CLI commands:
export AWS_CA_BUNDLE=~/.iamlive/ca.pem
You must also set the proxy settings for your session by running the following in the window executing your CLI commands:
export HTTP_PROXY=http://127.0.0.1:10080
export HTTPS_PROXY=http://127.0.0.1:10080
To enable proxy mode in the various AWS SDKs, you can run the following in the window executing your application prior to it starting:
For AWS SDKs:
export HTTP_PROXY=http://127.0.0.1:10080
export HTTPS_PROXY=http://127.0.0.1:10080
export AWS_CA_BUNDLE=~/.iamlive/ca.pem
Check the official docs for further details on setting the CA bundle.
To enable proxy mode in the Azure CLI or SDK, you can run the following in the window executing your application prior to it starting:
export HTTP_PROXY=http://127.0.0.1:10080
export HTTPS_PROXY=http://127.0.0.1:10080
export REQUESTS_CA_BUNDLE=~/.iamlive/ca.pem
To enable proxy mode in the Google Cloud CLI or SDKs, you can run the following in the window executing your application prior to it starting:
gcloud config set proxy/type http
gcloud config set proxy/address 127.0.0.1
gcloud config set proxy/port 10080
gcloud config set core/custom_ca_certs_file ~/.iamlive/ca.pem
I get a message "package embed is not in GOROOT" when attempting to build myself
This project requires Go 1.16 or above to be built correctly (due to embedding feature).
This project makes use of Parliament and was assisted by Scott Piper's CSM explainer. Thanks also to Noam Dahan's research into missing iam:PassRole dependant actions.