pws is a command-line password safe/manager written in Ruby using AES-256-CBC and PBKDF2.
Although the gem works well and as described, its cryptographic foundations have not been updated since 10 years ago and might not reflect current best practices.
Make sure your computer has Ruby installed.
You can then install pws with: $ gem install pws
Run $ pws --help for usage information.
If you use pws on Linux, you will need to have xsel or xclip installed (for the clipboard to work).
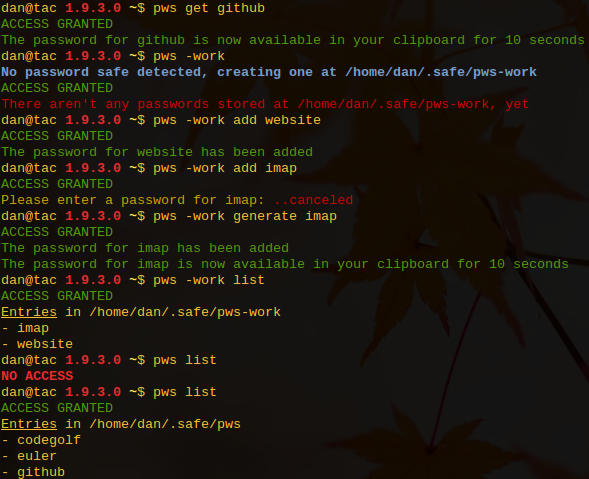
Besides using the --filename path/to/safe option, you can shortly call pws --cwd for using a .pws file in the current directory.
Check the .pws into version control and you have a great way to share a project's passwords within your team.
You should use a Ruby that was built with bindings to an openssl version >= 1.0 or pws will fall back to a Ruby-only version of the PBKDF2 function, which is much slower. If using openssl 1.0 is not possible for you, you can work around that issue by using the --iterations option with a value below 75_000 (see help). If you have problems using openssl 1.0 with your Ruby, please look for a solution in this issue.
The 0.9 password files are not compatible with the 1.0 version of pws, however, you can convert your safe with:
$ pws resave --in 0.9 --out 1.0
Trust the code by reading the source! It's originally based on this tutorial. You might want to start reading in the 0.9.2 tag, because it's got less features and therefore is less code.
- pws-otp Experimental OTP support for 2FA
- pwsqr Simple QR interface to pws gem. Helps to use your passwords on a smartphone.
- aws-pws A password-protected CredentialProvider for AWS
- omnivault Multi-platform keychain functionality
- Packaging ruby programs in NixOS using PWS as example
- namelessjon
- brianewing
- dquimper
- grapz
- thecatwasnot (cucumber specs loosely based on these)
- terabyte
- alex0112
© 2010-2021 Jan Lelis, MIT license