A remove command for AWS resources
This command line tool follows
the Unix Philosophy
of doing only one thing and doing it well:
It simplifies deleting over 250 AWS resource types across multiple accounts and regions.
Like other Unix-like tools, awsrm reveals its full power when combining it via pipes with other tools, such
as awsls for listing AWS resources and grep for filtering by resource
attributes.
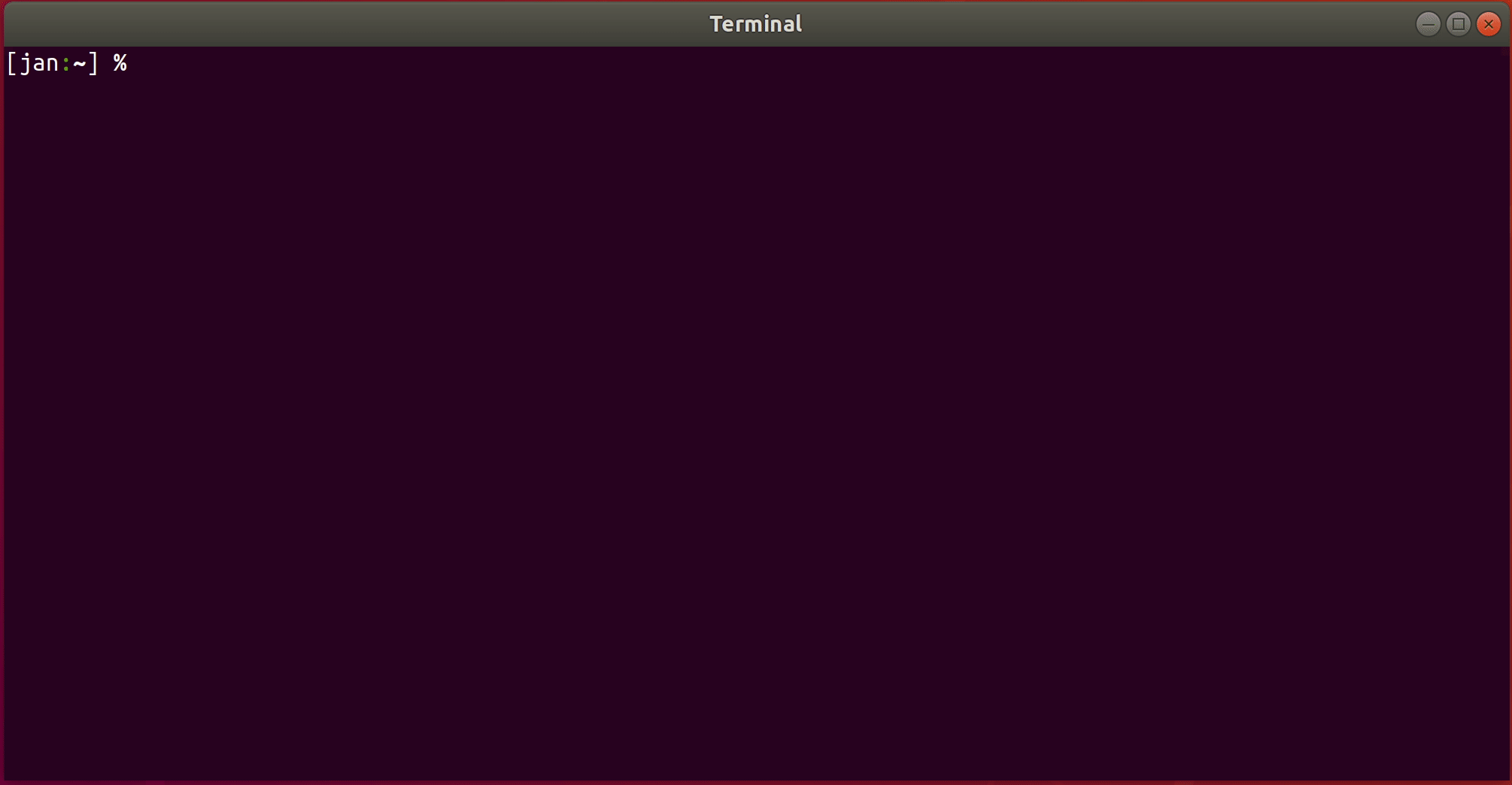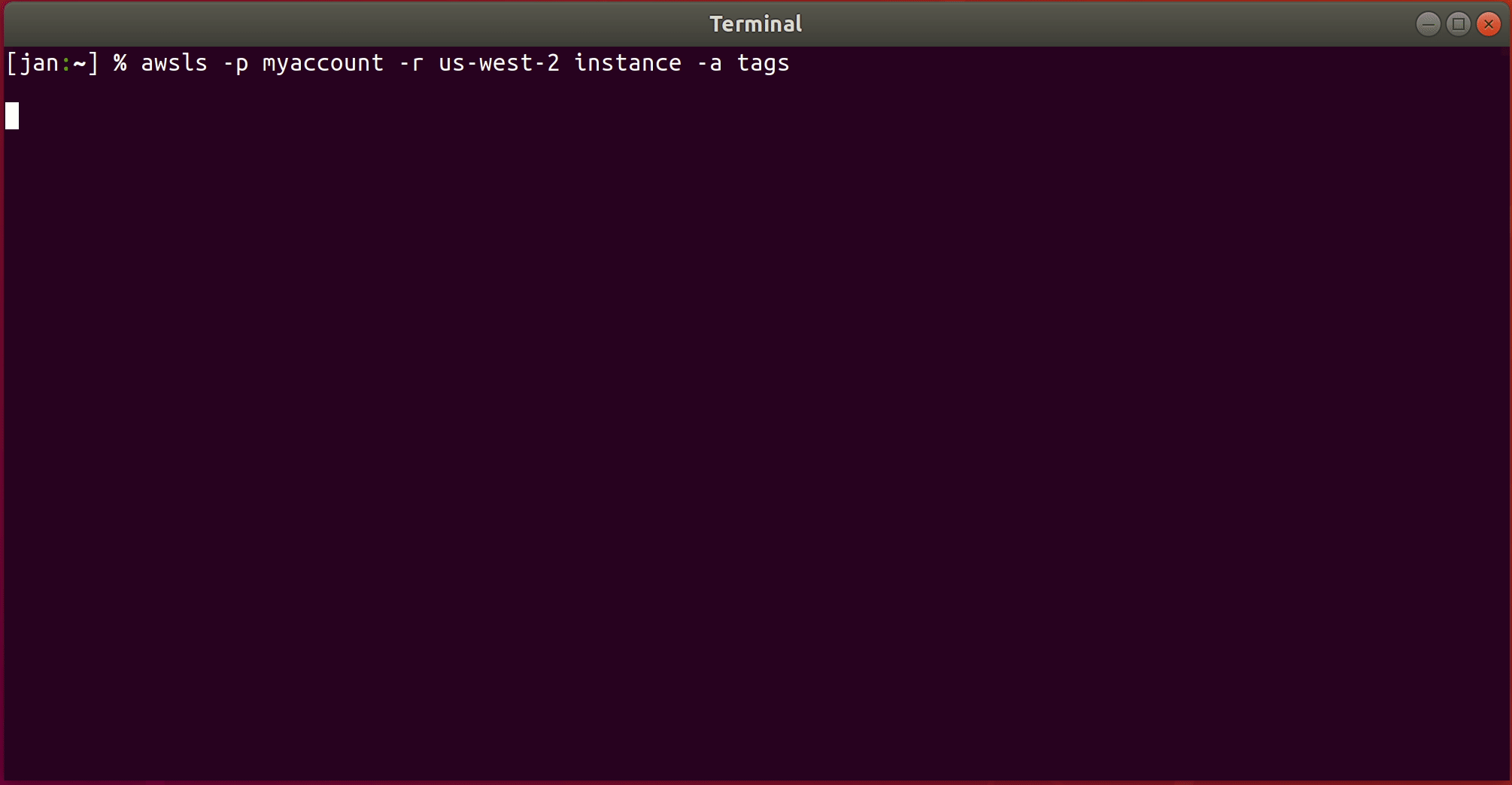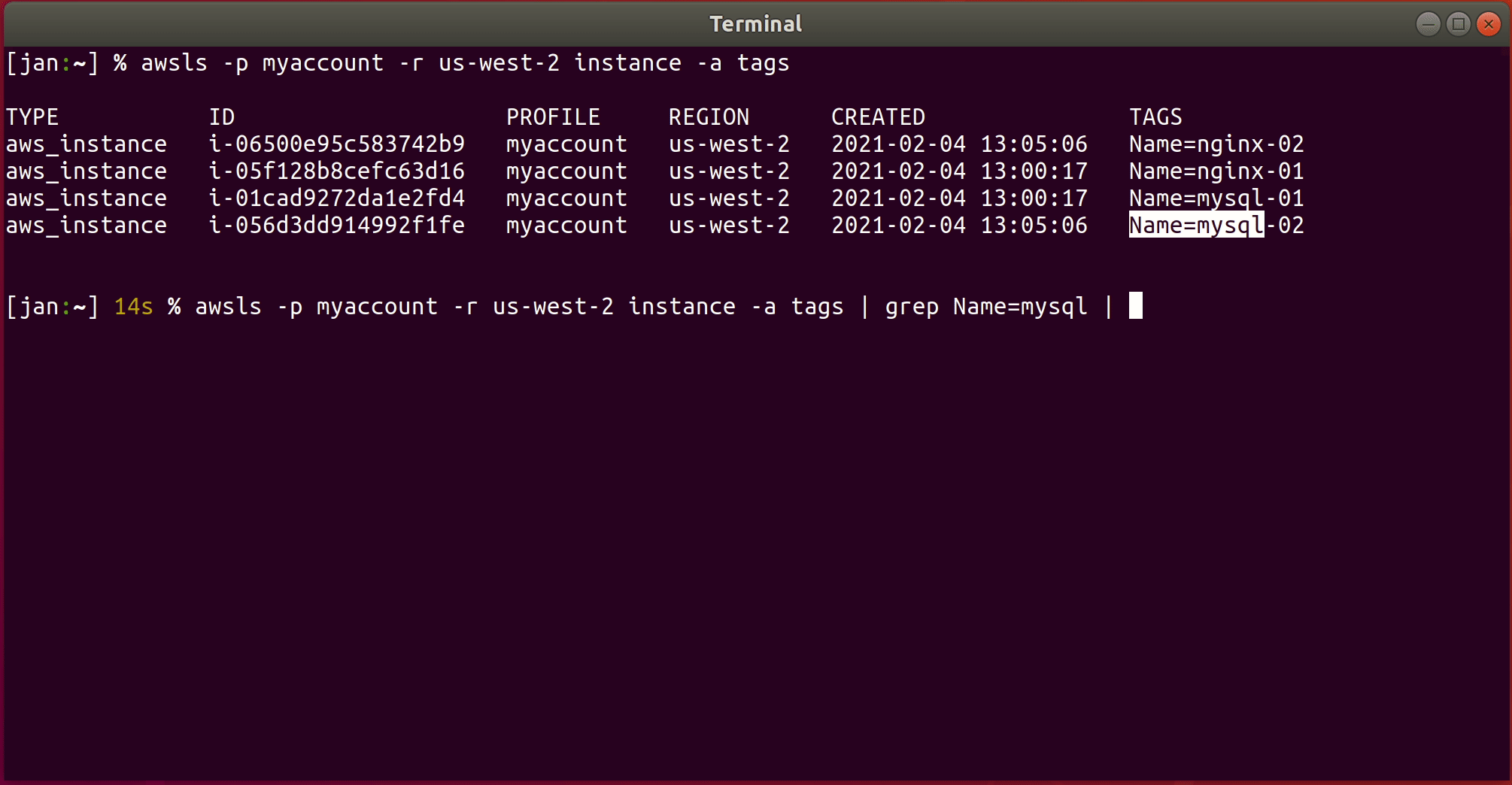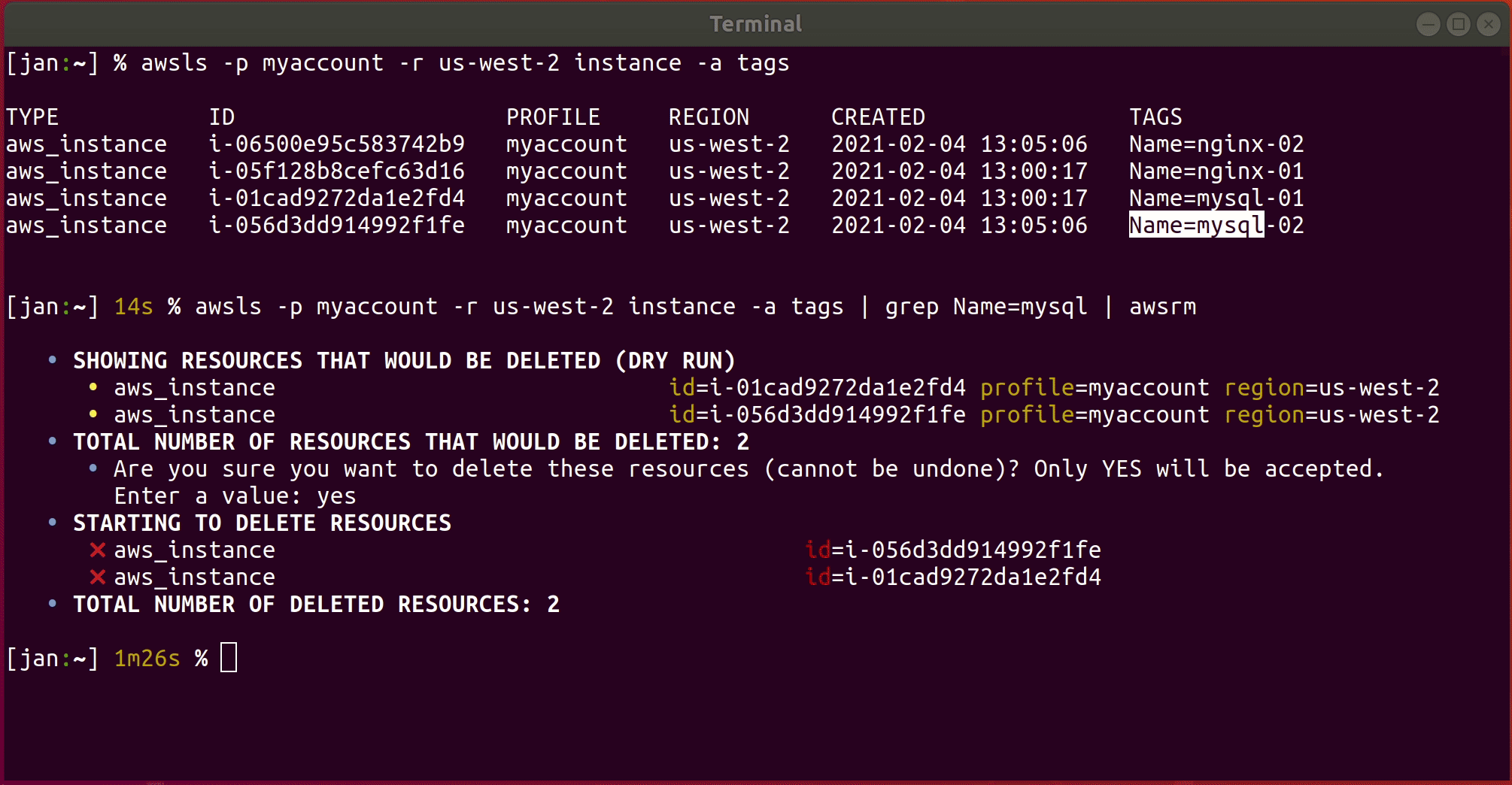
To delete, for example, all EC2 instances with tag Name=foo, run
awsls instance -a tags | grep Name=foo | awsrm
To filter on multiple attributes, display them with awsls via the -a (--attributes) <comma-separated list> flag.
Every attribute in the Terraform documentation
(here are
the attributes for aws_instance) can be used:
- List resources via
awslswith the attributes you want to filter on (here:-a tags) - Use standard tools like
grepto filter resources - Pipe result to
awsrm(nothing is deleted until you confirm)
Note: awsls output passes on profile and region information, so that awsrm knows for each resource in what
account and region to delete it.
Depending on the type of resource, deletion can take some time. This GIF runs faster than EC2 instances are actually terminated; the shell prompt shows the real execution times in seconds.
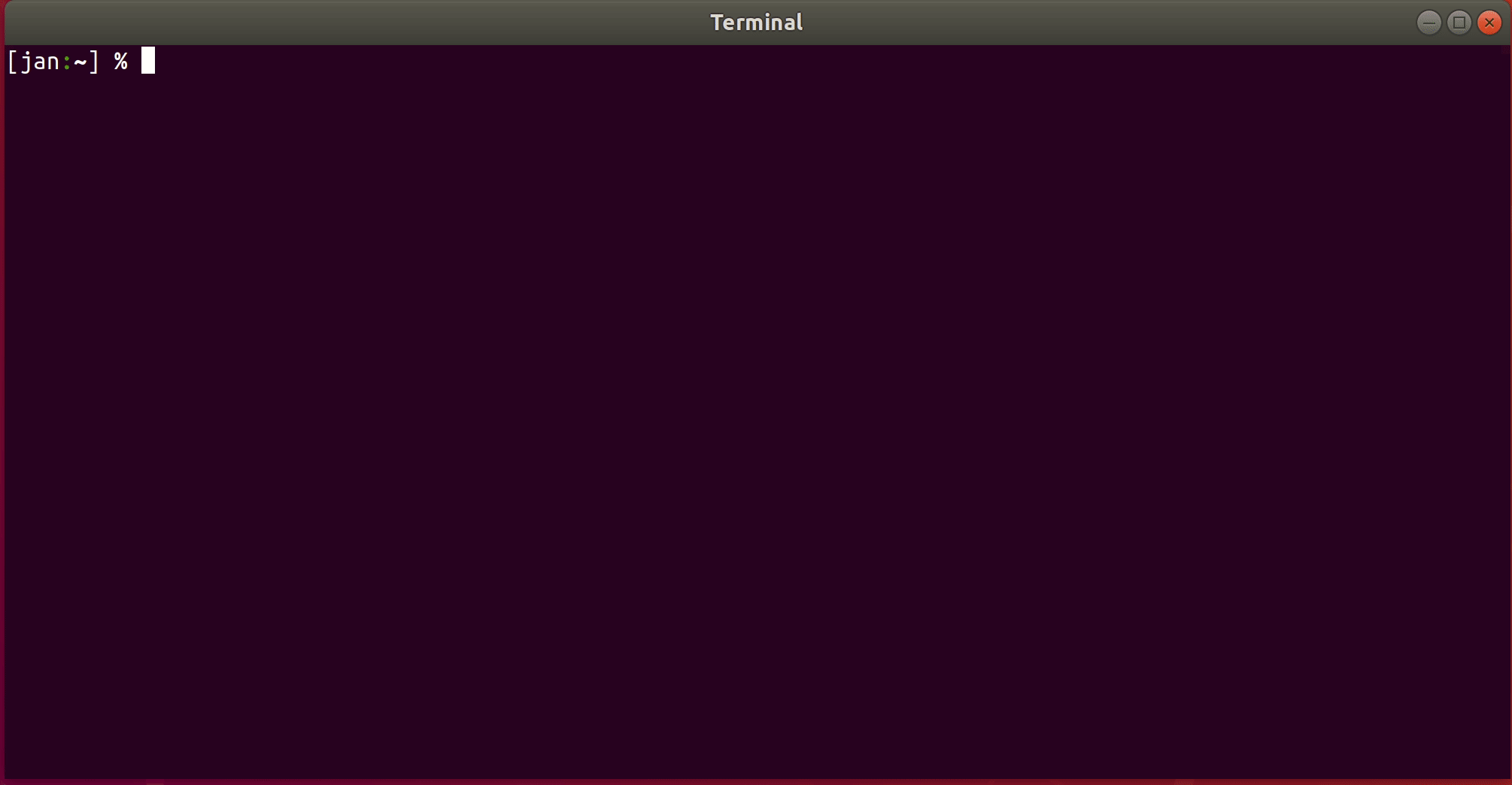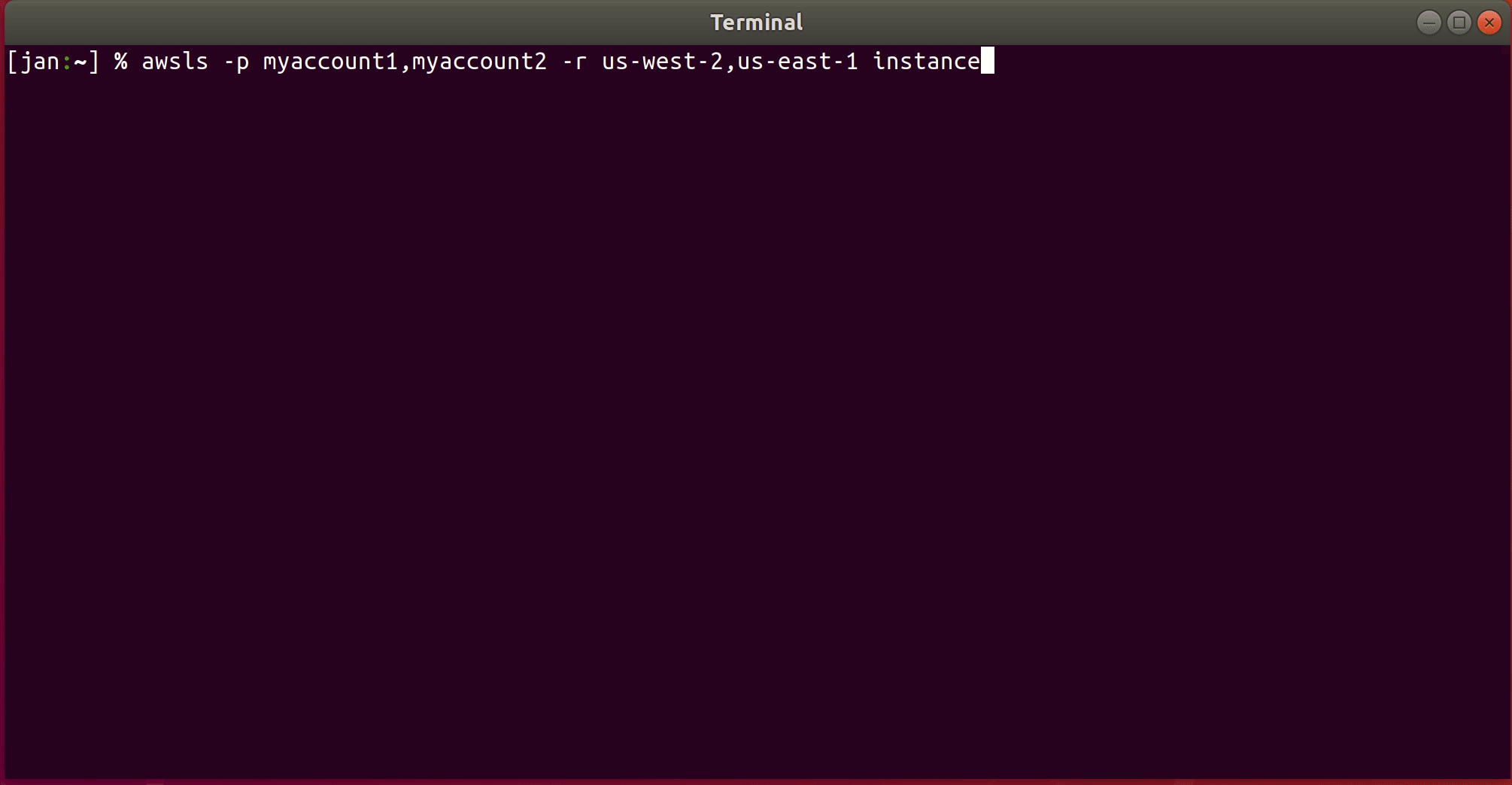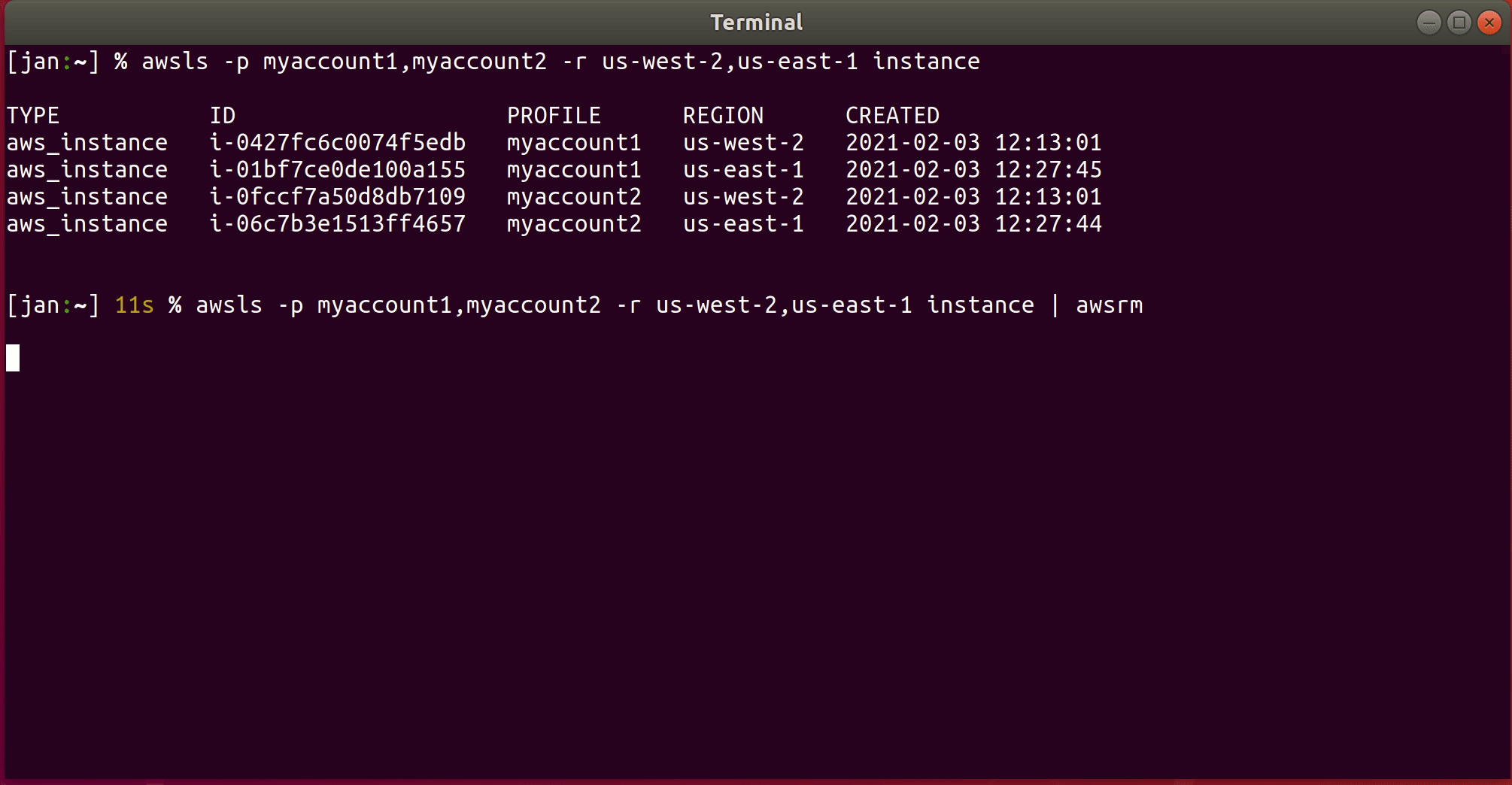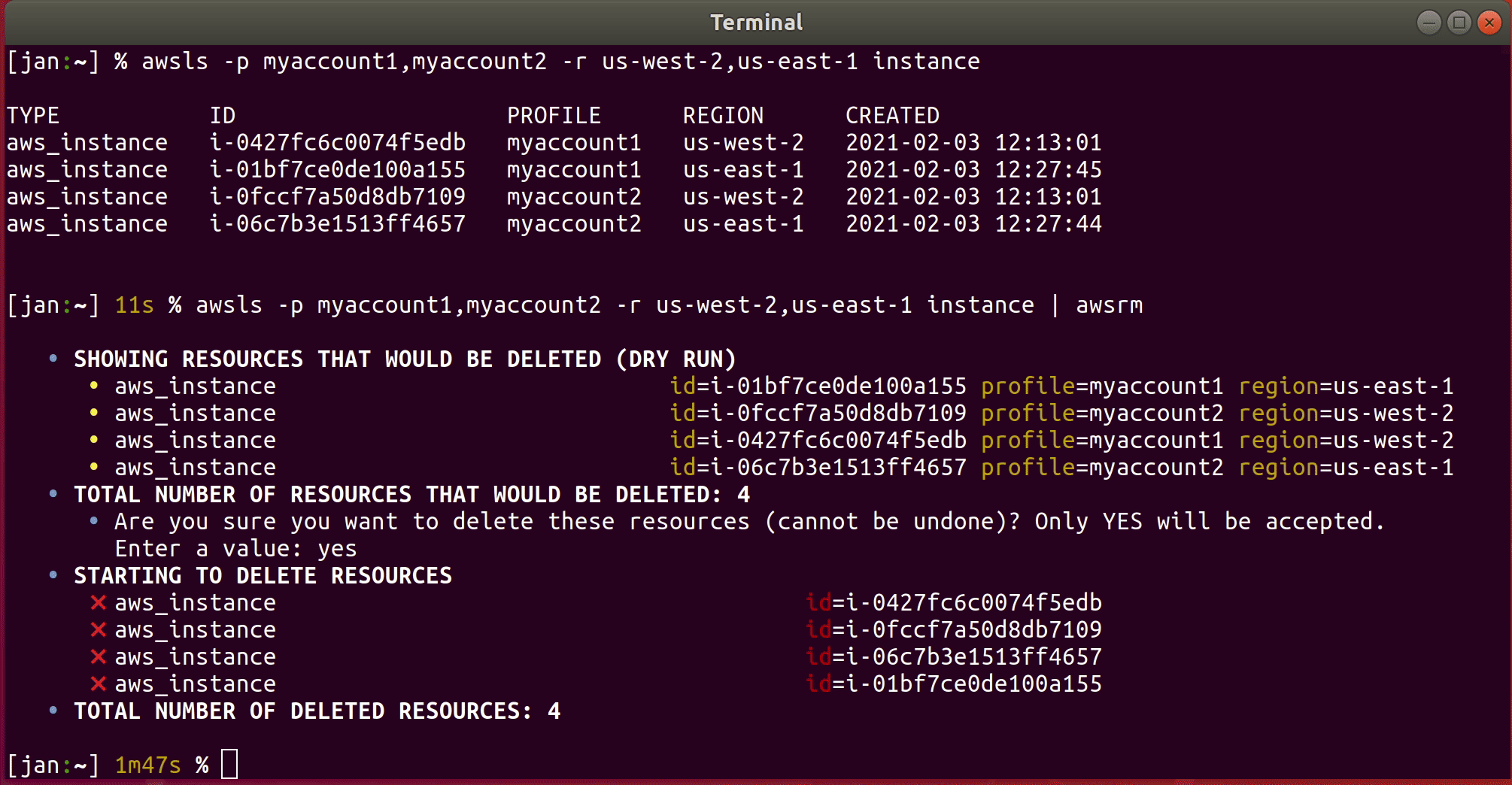
List all instances with awsls in the AWS accounts associated with profile myaccount1 and myaccount2 in both
regions us-west-2 and us-east-1 and pipe the result to awsrm:
awsls -p myaccount1,myaccount2 -r us-west-2,us-east-1 instance | awsrm
Delete specific resources by ID, for example, some IAM roles
awsrm iam_role db-cluster elb nginx
or VPCs
awsrm vpc vpc-1234 vpc-3456 vpc-7689
- List resources via
awslsto find out what resources to delete. - Use
awsrmto delete the resources by resource type and ID(s)
Input via arguments:
awsrm [flags] <resource_type> <id> [<id>...]
Input via pipe:
awsls [flags] <resource_type> | awsrm
or
echo "<resource_type> <id> <profile> <region>" | awsrm
To see options available run awsrm --help.
You can download a specific version on the releases page or use the
following way to install to ./bin/:
curl -sSfL https://raw.githubusercontent.com/jckuester/awsrm/master/install.sh | sh -s v0.2.0Homebrew users can install by:
brew install jckuester/tap/awsrmFor more information on Homebrew taps please see the tap documentation.
This tool can not only delete any resource type that is supported by awsls, but any resource type covered by the Terraform AWS Provider.
Note: the prefix aws_ for resource types is optional. This means, for example, awsrm aws_instance <id> and
awsrm instance <id> are both valid commands.
You are using this tool at your own risk! I will not take responsibility if you delete any critical resources in your production environments.