_ _____ _ _____ _ _ ____ _____ _ _____ _ _ _ _ _ _ _____ ___ _ _ ____
| |/ / _ \| | |_ _| | | | _ \| ____| / \|_ _| | | | | | | | \ | |_ _|_ _| \ | |/ ___|
| ' | | | | | | | | |_| | |_) | _| / _ \ | | | |_| | | | | \| | | | | || \| | | _
| . | |_| | |___ | | | _ | _ <| |___ / ___ \| | | _ | |_| | |\ | | | | || |\ | |_| |
|_|\_\__\_|_____| |_| |_| |_|_| \_|_____/_/ \_|_| |_| |_|\___/|_| \_| |_| |___|_| \_|\____|
This repository is an effort to provide ready-made detection and hunting queries (and more) in order to help analysts and threat hunters harness the power of KQL in Microsoft Sentinel and Microsoft 365 Defender.
Please:
- Read the Disclaimer below.
- If you found a useful query here, consider giving a ⭐ to this repository.
Enjoy, and please reach out for any concerns and suggestions: cyb3rmik3.
If Microsoft Sentinel and Microsoft 365 Defender are your daily to-go tools, you should consider following Microsoft's Certified Security Operations Analyst course (Exam code SC-200). You will be acquainted with Microsoft's wide range of Security products and how you can use them to provide data, security signal and analyze alerts and incidents.
Be that as it may, you can jump into Microsoft's course that focus on KQL:
Data is organized into a hierarchy of databases, tables and columns, similar to SQL. For example, the DeviceNetworkEvents table in the advanced hunting schema contains information about network connections and related events.
where filters on a specific predicate
DeviceNetworkEvents
| where LocalIP == "192.168.0.1"
- Contains: Looks for any substring match
- Has: Looks for a specific word (better performance)
DeviceNetworkEvents
| where DeviceName has "ComputerName"
Returns the time offset relative to the time the query executes
DeviceNetworkEvents
| where Timestamp > ago(1d)
Selects the columns to include in the order specified
DeviceNetworkEvents
| where Timestamp > ago(1d)
| where DeviceName has "ComputerName"
| project Timestamp, ActionType, RemoteIP, RemotePort, RemoteUrl
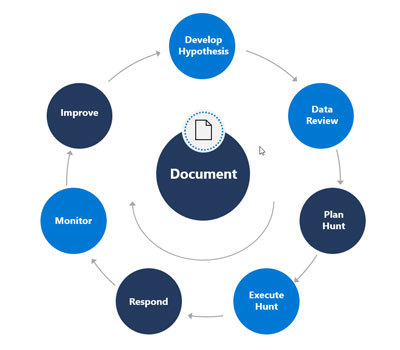
Threat hunting should be a continual process. We start at the top of our cycle with our Hypothesis. Our Hypothesis helps us plan out what we are going to hunt for, which requires us to understand where we're going to hunt and how we'll do it. This means we need to understand the data we have, the tools we have, the expertise we have, and how to work with them. The hunting cycle doesn't stop when we execute the hunt. There are still several phases we need to conduct throughout the life cycle, including responding to anomalies. Even if we don't find an active threat, there will be activities to perform. More.
The approach to hunting has two components: Characterization of malicious activity, and hunt Execution. These components should be ongoing activities, continuously updated based on new information about adversaries and terrain. More.
The KQL queries in this GitHub repository are provided for informational purposes only. Users are solely responsible for their usage and should exercise caution. It is advised to thoroughly understand and test the queries before implementing them in a production environment.