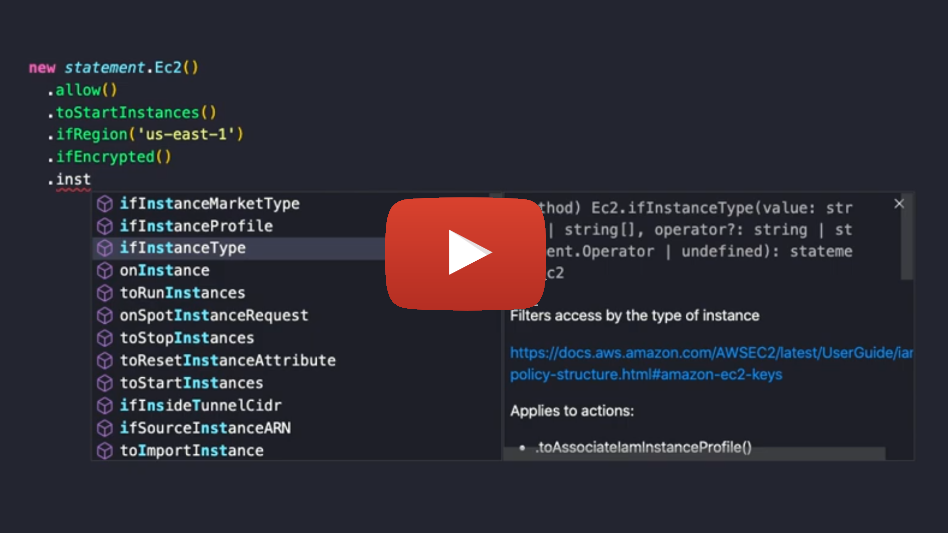
AWS IAM policy statement generator with fluent interface.
Support for:
- 401 Services
- 17042 Actions
- 1823 Resource Types
- 1782 Condition keys
This is an early version of the package. The API will change while I implement new features. Therefore make sure you use an exact version in your package.json before it reaches 1.0.0.
Find the documentation at Read the Docs.
There are two different package variants available:
-
iam-floyd: Can be used in AWS SDK or for whatever you need an IAM policy statement for
-
cdk-iam-floyd: Integrates into AWS CDK and extends
iam.PolicyStatementStarting with version 0.300.0, the packages are compatible with CDK v2. For CDK v1 you can use any version up to:
Find them all on libraries.io.
| CDK | cdk-iam-floyd |
|---|---|
| <= 1.151.0 | <= 0.285.0 |
| >= 1.152.0 | 0.286.0 |
| >= 1.158.0 | No compatible version! |
| >= 2.0.0 | >= 0.300.0 |
| >= 2.20.0 | >= 0.351.0 |
| >= 2.26.0 | >= 0.377.0 |
| 2.29.x | No compatible version! |
| >= 2.30.0 | >= 0.391.0 |
The code contained in the lib/generated folder is generated from the AWS documentation. The class- and function-names and their description therefore are property of AWS.
AWS and their services are trademarks, registered trademarks or trade dress of AWS in the U.S. and/or other countries.
This project is not affiliated, funded, or in any way associated with AWS.
IAM Floyd is licensed under Apache License 2.0. Dependencies might be released under different licenses.