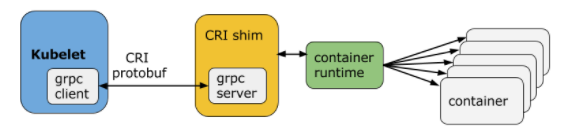
KubeVirt is a virtual machine management add-on for Kubernetes. The aim is to provide a common ground for virtualization solutions on top of Kubernetes.
At its core, KubeVirt extends Kubernetes by adding
additional virtualization resource types (especially the VM type) through
Kubernetes's Custom Resource Definitions API.
By using this mechanism, the Kubernetes API can be used to manage these VM
resources alongside all other resources Kubernetes provides.
The resources themselves are not enough to launch virtual machines. For this to happen the functionality and business logic needs to be added to the cluster. The functionality is not added to Kubernetes itself, but rather added to a Kubernetes cluster by running additional controllers and agents on an existing cluster.
The necessary controllers and agents are provided by KubeVirt.
As of today KubeVirt can be used to declaratively
- Create a predefined VM
- Schedule a VM on a Kubernetes cluster
- Launch a VM
- Stop a VM
- Delete a VM
Try our quickstart at kubevirt.io.
See our user documentation at kubevirt.io/docs.
Once you have the basics, you can learn more about how to run KubeVirt and its newest features by taking a look at:
To set up a development environment please read our Getting Started Guide. To learn how to contribute, please read our contribution guide.
You can learn more about how KubeVirt is designed (and why it is that way), and learn more about the major components by taking a look at our developer documentation:
- Architecture - High-level view on the architecture
- Components - Detailed look at all components
- API Reference
The KubeVirt SIG-release repo is responsible for information regarding upcoming and previous releases.
- KubeVirt to Kubernetes version support matrix - Verify the versions of KubeVirt that are built and supported for your version of Kubernetes
- Noteworthy changes for the next KubeVirt release - Pre-release notes for the upcoming release
- Release schedule - For our current and previous releases
If you got enough of code and want to speak to people, then you got a couple of options:
- Follow us on Twitter
- Chat with us on Slack via #virtualization @ kubernetes.slack.com
- Discuss with us on the kubevirt-dev Google Group
- Stay informed about designs and upcoming events by watching our community content
When sending patches to the project, the submitter is required to certify that they have the legal right to submit the code. This is achieved by adding a line
Signed-off-by: Real Name <[email protected]>
to the bottom of every commit message. Existence of such a line certifies that the submitter has complied with the Developer's Certificate of Origin 1.1, (as defined in the file docs/developer-certificate-of-origin).
This line can be automatically added to a commit in the correct format, by using the '-s' option to 'git commit'.
KubeVirt is distributed under the Apache License, Version 2.0.
Copyright 2016
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.